There are many configuration scenarios for Authentication in SANnav. They all revolve the following.
What is the Primary Authentication mechanism for SANnav. What is the Secondary Authentication mechanism and what System is handling Authorization for access to capabilities in SANnav.
We will be setting up the Authentication as follows.
- Primary Authentication – LDAP Server (Domain Controllers)
- Secondary Authentication – SANnav
- Authorizing System – Authentication Server Groups
You will need the following information
- Pre-Created AD Groups
- A list of your Domain Controllers with the closest proximity DCs at the top
- Credentials to "Fetch" from AD
In my example I use an existing group but you would most likely want to define these groups specifically for the SANnav roles assigned.
- SANnav_Operator
- SANnav_SAN_System_Administrator
- SANnav_Security_Administrator
And so on..
If you use AORS you may have another level in the naming so you can distinguish the role to AOR combination.
i.e. SANnav_AORName_Operator
These are just examples. Naming is super important so spend some time on the naming if you don’t already have a scheme in place.
TL/DR
Navigate to the SANnav Authentication and Authorization.
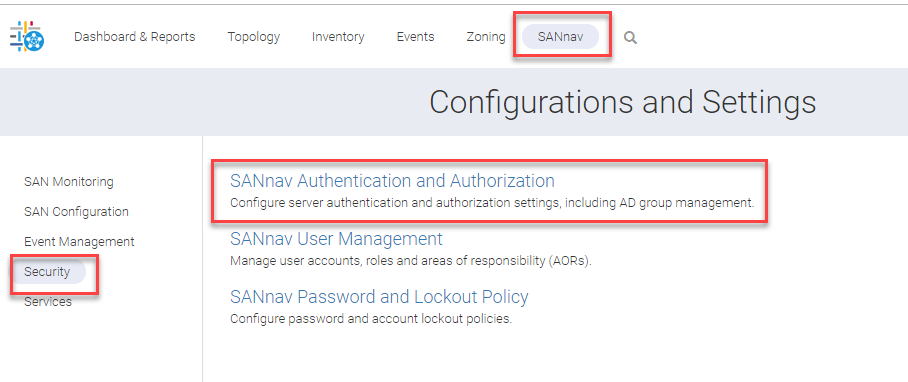
We are going to setup LDAP authentication and leverage LDAP groups to assign SANnav native roles to. We want the Selections to look like the picture below.
Be sure to use your LDAP (Domain Controllers) server list with the closest DCs to the SANnav server at the top of the list.
When you add the DCs you are given an open to use SSL. I would try to implement SSL first and fail back to 389 if you have issues after completion.
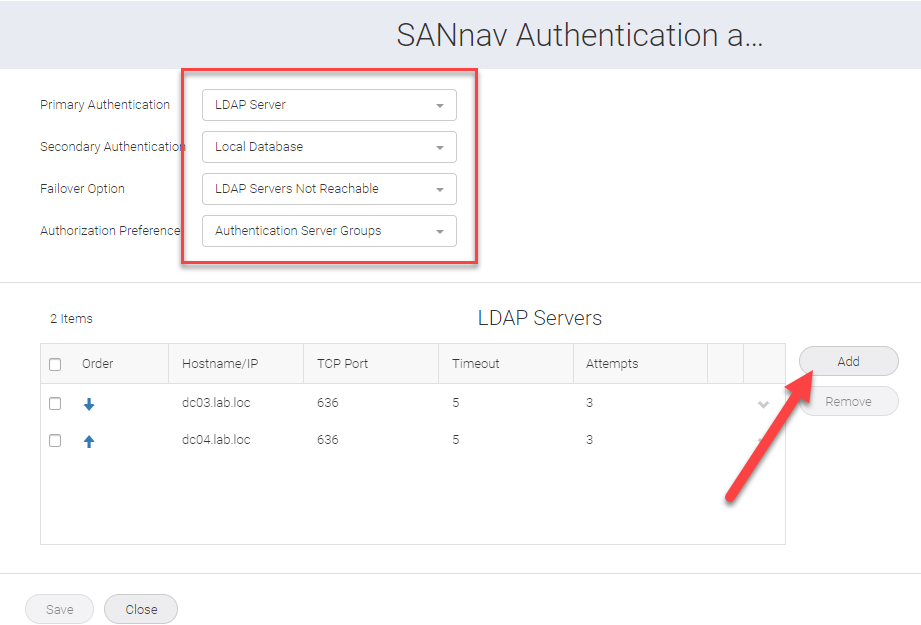
The servers cannot be edited after adding so you would have to add new servers with no SSL and delete the old entries.
Save this
Click on the SANnav User Management Link
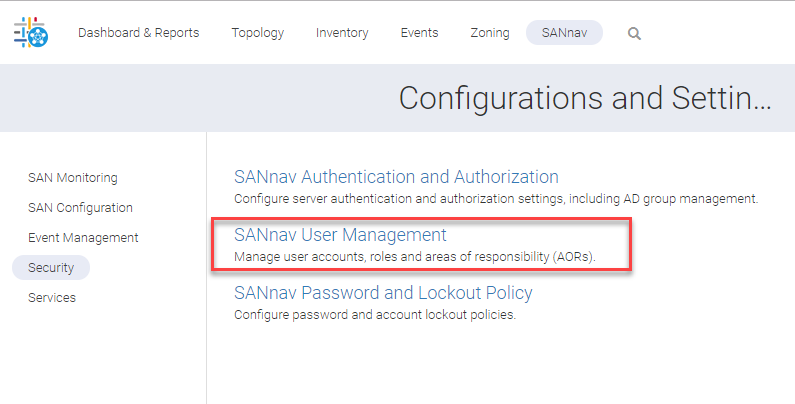
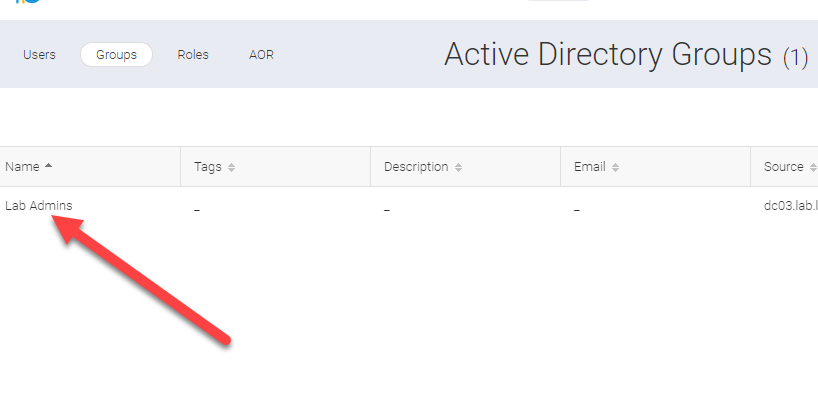
Since we are leveraging AD groups we will import these AD groups into SANnav and assign the SANnav AOR and roles to them inside of SANnav.
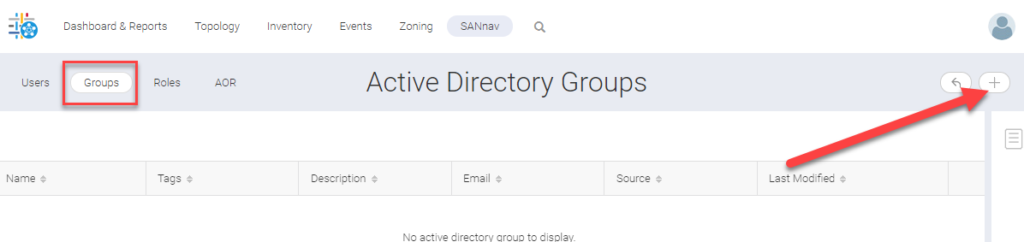
Fetch the AD group which you will be assigning roles
The user specified here must be able to
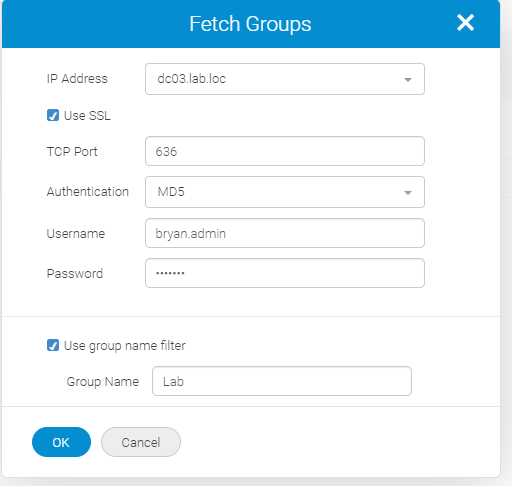
Click on the group to edit the properties and assign roles and AORs
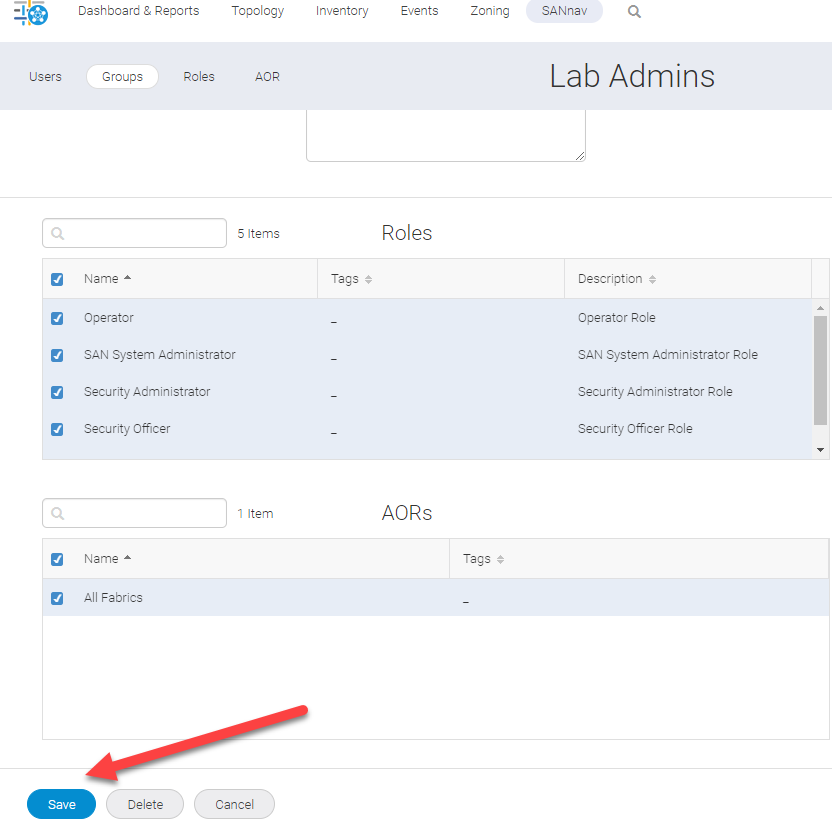
Check all of the boxes required for your AD Group role.
This is the lab so I check them all. Set these up to meet the security and capability needs of your teams.
Then press save.
Log out and test credentials from a member of your AD group.
Do not use the domain in the username field.

And there you have it.