Below outlines an example implementation of Active Directory integration with Ansible Tower.
Goal..
We want to have a new org implemented in Tower tied to AD groups and Teams built to assign permissions to Job Templates.
- You will need an account that can read from LDAP – Domain User
- A group to allow normal user access to tower
- A group granting auditor rights
- Go ahead and create this. if you don’t need it don’t use it but it may come in handy one day and it will already be in place.
- Create an admin group for System Admin access – Overall Access
- An example Team group is created in this example for granting job template permissions later
Create the needed groups in AD.
The group layout will be like this.
- "<tower>_<org>_<roles>"
- "<tower>_<org>_team_<team>"
In my case I am setting up an org for the lab so the groups will be named the following.
- tower_lab_users
- Everyone who login to Tower
- tower_lab_auditors
- System Auditor
- tower_lab_admins
- System Admin
- tower_lab_team_helpdesk
- Example Team
Get Groups Distinguished Names
Query these groups in AD so you can get the DNs for the copy and paste actions
get-adgroup -Filter {Name -like "lab_tower_*"} | ft distinguishedName
You will be using these to copy and paste in to the fields later.
Create the AD Bind User
Create your AD ldap_user for binding and get the upn.
Configure Authentication in Tower
Below are the fields we will fill in..
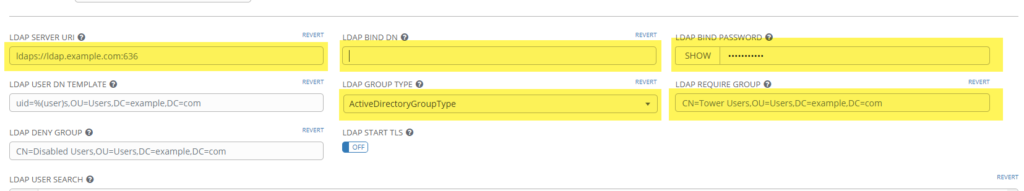
Example fields below..
You will need the DNs from earlier and the ldap_user UPN..
LDAP SERVER URI
ldaps://dc01.yourdomain.com:636 ldaps://dc02.yourdomain.com:636
Here I list two DCs. You can list whichever. Just try to make them in close proximity to the Tower server. These entries are separated by spaces. I think commas work too.
The LDAPS is also used. You may have issues with certificate trusts due to an enterprise CA. If that happens do the following.
Export the root CA from a valid cert path as Base64 encoded. Copy as pem file to /etc/pki/ca-trust/source/anchors/ on the tower server then run "update-ca-trust".
LDAP BIND DN
ldap_user@yourdomain.com
LDAP BIND PASSWORD
ldap_user's password
LDAP GROUP TYPE
ActiveDirectoryGroupType
LDAP REQUIRE GROUP
DN from the tower_lab_users i.e.
CN=lab_tower_users,OU=Groups,DC=yourdomain,DC=com
The next fields will look like the image below.
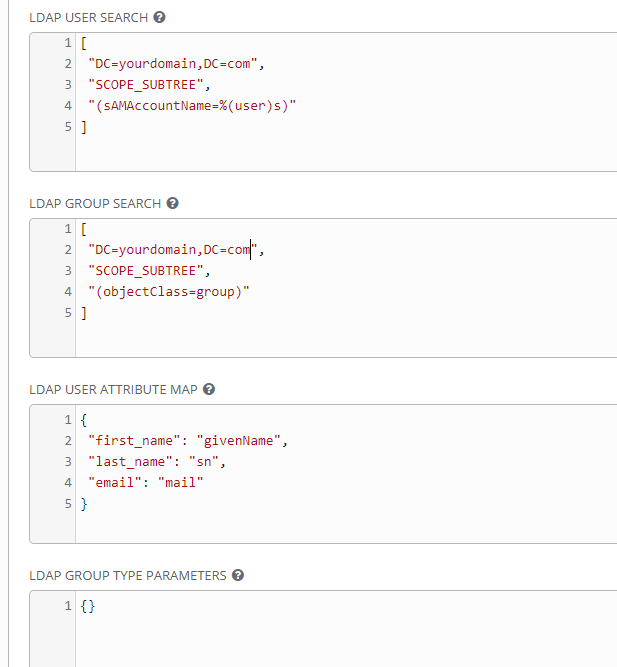
Here are field snippets to help you with the list syntax
LDAP USER SEARCH
["DC=yourdomain,DC=com","SCOPE_SUBTREE","(sAMAccountName=%(user)s)"
]
LDAP GROUP SEARCH
["DC=yourdomain,DC=com","SCOPE_SUBTREE",
"(objectClass=group)"]
LDAP USER ATTRIBUTE MAP
{"first_name": "givenName","last_name": "sn","email": "mail"}
LDAP GROUP TYPE PARAMETERS
{}
Now we get crazy with the JSON. I have simply provided the snippets here as the JSON does not look good in the fields themselves.
The below fields will set the group access, teams and orgs.
LDAP USER FLAGS BY GROUP
this one sets the lab_tower_admins to system admins and the lab_tower_auditors to system_auditors
{"is_superuser": [
"CN=lab_tower_admins,OU=Groups,DC=yourdomain,DC=com"
],"is_system_auditor": ["CN=lab_tower_auditors,OU=Groups,DC=yourdomain,DC=com"]
}
LDAP ORGANIZATION MAP
this one will setup the admins and the user groups in the org.
I suck at WordPress so formatting is not greatI know.. Just copy and paste in between the quotes and or clean it up in an edit before.
- {
- "LDAP Lab": {
- "admins": "CN=lab_tower_admins,OU=Groups,DC=yourdomain,DC=com",
- "remove_admins": true,
- "users": [
- "CN=lab_tower_auditors,OU=Groups,DC=yourdomain,DC=com",
- "CN=lab_tower_users,OU=Groups,DC=yourdomain,DC=com",
- "CN=lab_tower_team_helpdesk,OU=Groups,DC=yourdomain,DC=com"
- ]
- }
- }
LDAP TEAM MAP
this one maps out the Teams to the AD groups.
The key is the Team Name. Each Key value will come in as a Team in Tower with the members of the AD Group specified in the DN. Only as the users login.
{
"LDAP Lab Admins": {
"organization": "LDAP Lab",
"users": "CN=lab_tower_admins,OU=Groups,DC=yourdomain,DC=com",
"remove": true
},
"LDAP Lab Auditors": {
"organization": "LDAP Lab",
"users": "CN=lab_tower_auditors,OU=Groups,DC=yourdomain,DC=com",
"remove": true
},
"LDAP Lab Users": {
"organization": "LDAP Lab",
"users": "CN=lab_tower_users,OU=Groups,DC=yourdomain,DC=com",
"remove": true
},
"LDAP Lab HelpDesk": {
"organization": "LDAP Lab",
"users": "CN=lab_tower_team_helpdesk,OU=Groups,DC=yourdomain,DC=com",
"remove": true
}
}
Configure AD Group Membership
You will need to have everyone first in the lab_tower_users groups so that they can first have access. Then you use the Teams groups to grant place them in the Teams.
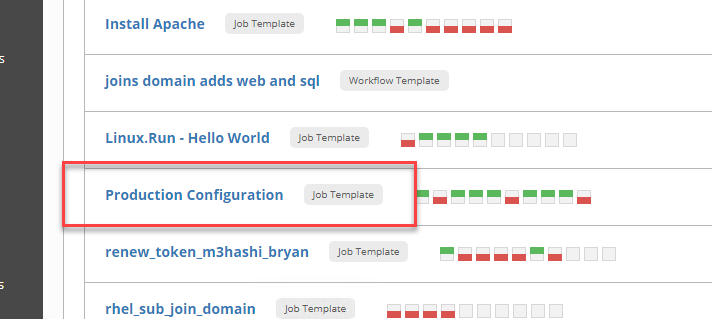
i.e. HelpDesk member Cory Needs to Access to do base installs and configure the new installs with all of the production requirements.
He needs to run the Job Template below.
I first added Cory to the AD groups required.
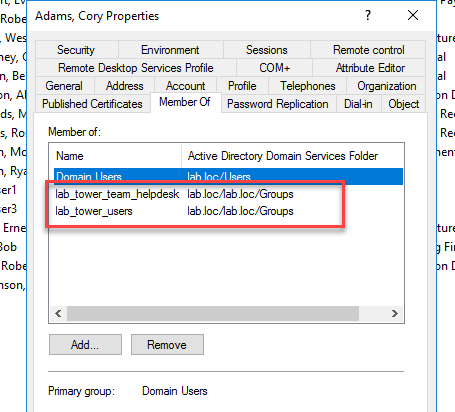
Then I have him login or I use a test account in the same group to login. This is required because the Team will only be created when someone in that group logs in to Tower.
I have Cory log in and we now see the Team.
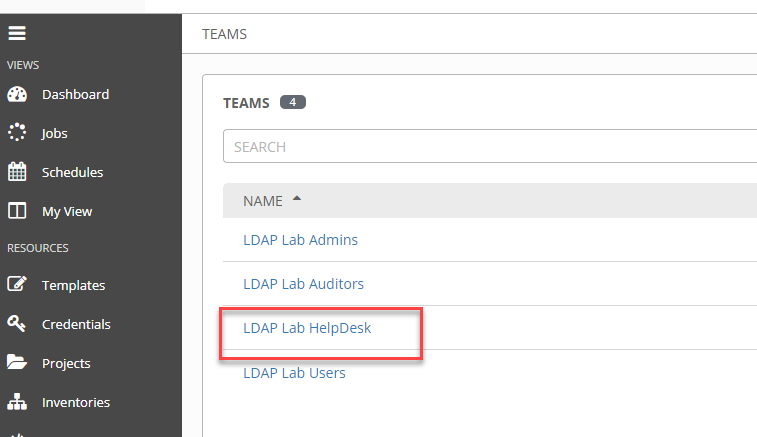
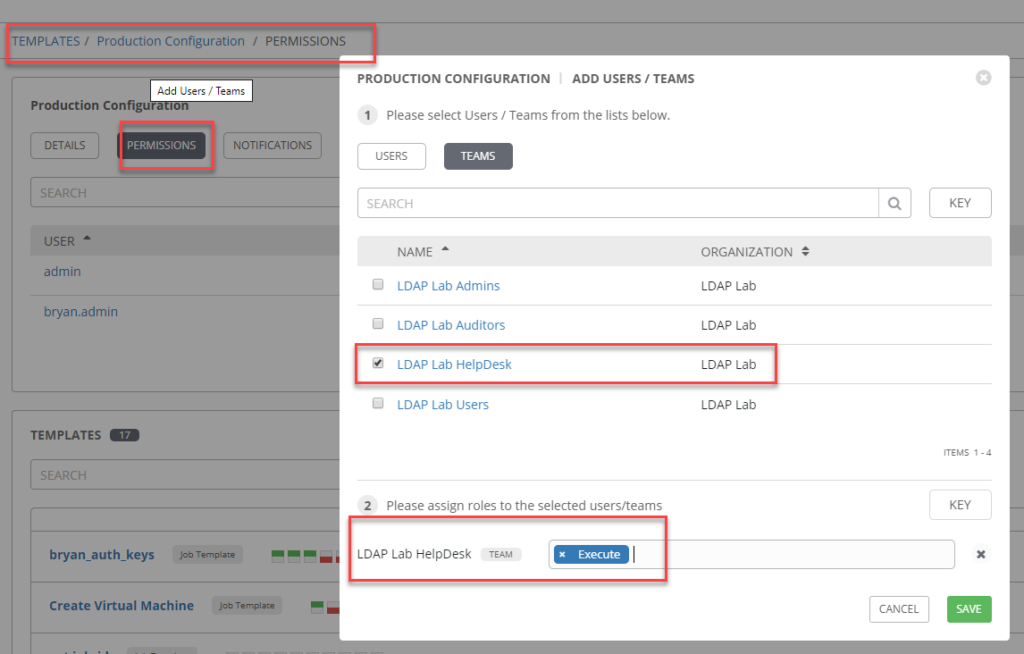
Grant Team access to the Template.
Log in as admin or better yet a member of the tower_lab_admins AND the tower_lab_users group to grant Team permissions.
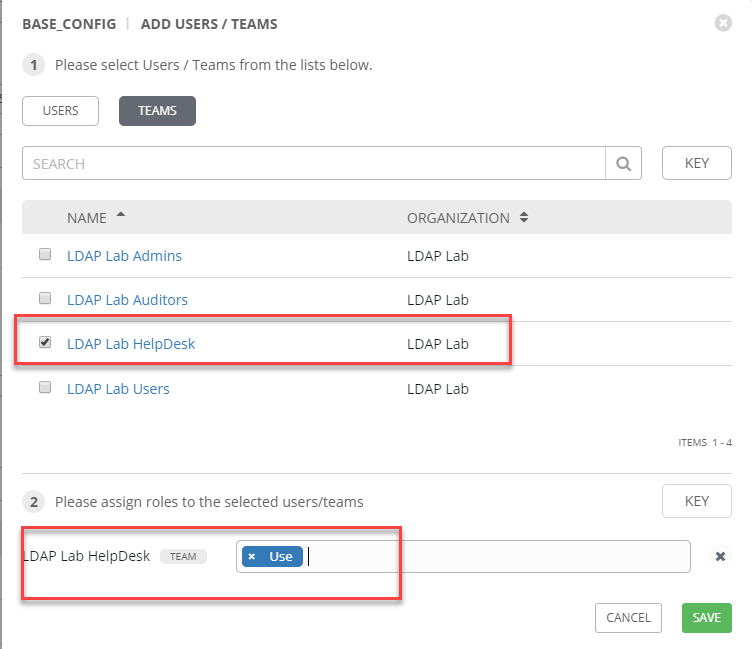
You will also need to grant this Team access to inventory. Inventory can take a post of its own but for brevity I assume you have an inventory object with some hosts. Navigate there and grant permissions to the inventory.
https://docs.ansible.com/ansible-tower/latest/html/userguide/inventories.html
Now have Cory log out and back in and….
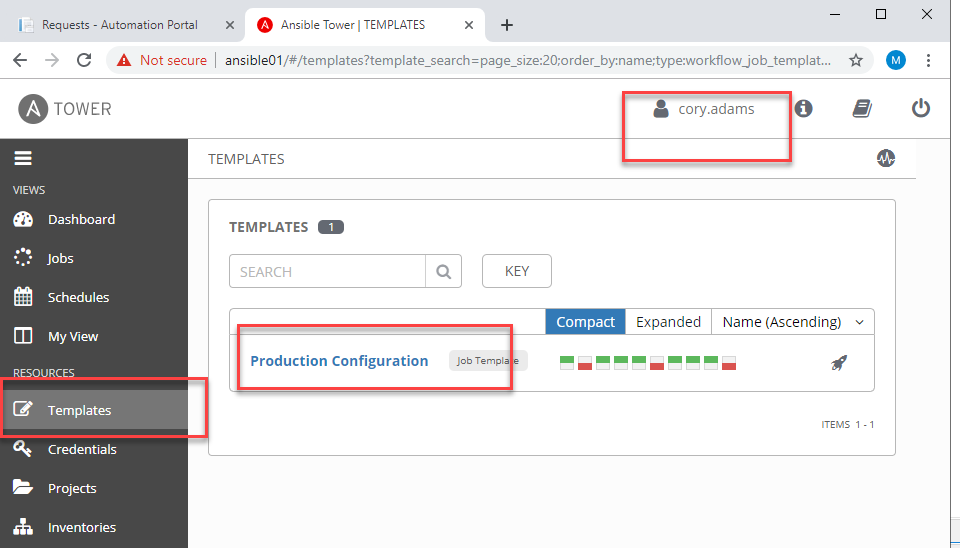
This pretty much covers a lot of implementation cases for Tower where you would like to leverage AD groups to grant permissions to Jobs.
One very important thing… These groups need to be put some place where they will not be moved intentionally. The DNS are fully qualified paths to the object in AD. AD admins tend to move things around time to time so an OU dedicated and labeled with BIG LETTERS, to easily identify these would be preferred.

